In today’s digital economy, data is the driving force behind innovation, helping us make smarter decisions and stay ahead of the competition. Yet, data can easily be compromised, leading to costly financial setbacks and lasting reputational damage.
That’s why customers and partners are more cautions about who they trust with their sensitive information. For businesses, it’s no longer enough to simply handle data – they need to prove they can keep it safe. This shift has transformed data governance and data security from ‘nice-to-haves’ to essential pillars of business operations.
Data governance VS data security: what’s the difference, and why you need both?
Terms like data governance and data security are often used interchangeably, but while they work hand in hand, each plays a unique role in a company’s data strategy.
Data governance is all about setting up internal policies, procedures, and frameworks that define who owns the data, who can access it, and how it’s used. This keeps data organized, consistent, and reliable, helping businesses maintain control over their most important information and prevent employee misuse or accidental mishaps.
A strong data governance structure also opens the door to data democratization, giving users broader access to data while ensuring compliance with established standards. For instance, systems like data mesh break down master data into manageable units, which can be widely accessible to the people who need them, while modifications remain in the hands of a few who have full ownership.
Data security, on the other hand, focuses on protecting data from external threats, both when it’s stored and when it’s exchanged. Techniques such as encryption come into play here, scrambling sensitive information into unreadable code to safeguard it from unauthorized access.
But here’s the thing: without proper governance, data security is like locking your doors without knowing who holds the keys.
So, how can companies make sure their governance and security framework is up to par?
The 6 pillars of data governance and security
There are software solutions that can provide companies with the highest standards of security and encryption at every stage of the data lifecycle, while fostering collaboration between teams.
Rulex Platform is designed to meet these critical needs, supporting the creation of a strong, reliable data governance and security framework through six main capabilities:
- Data catalogs. Rulex Platform supports data mesh systems, facilitating the creation of sub-catalogs within the user’s preferred cloud environment and enabling resources to be accessed via a shareable yet encrypted username and password.
- Clear data ownership. Rulex Platform provides granular control over roles and permissions, which can be assigned to individual users or groups. This means users can decide exactly who gets to see, execute, or delete specific resources, preventing any unauthorized or accidental mishaps.
- Policy monitoring. Rulex Platform automatically logs all access to and operations performed within the software. Modifications to the settings and preference files are also logged and encrypted to prevent external alteration.
- Event logs. Rulex Platform supports security information and event management (SIEM) technology for log event collection and real-time analysis of security alerts, simplifying compliance tracking and prioritizing incident response efforts.
- Advanced encryption. Rulex Platform uses the latest and most advanced TLS 1.3 protocol and AES-256-GCM encryption to protect data at rest and in motion. Users can choose to have encryption keys generated automatically or provide their own, giving the flexibility to match specific security needs.
- External vault systems integration. Rulex Platform securely stores sensitive configuration data within its environment or through external vault systems, allowing real-time retrieval of credentials and secrets without embedding them in source code, minimizing the risk of exposure.
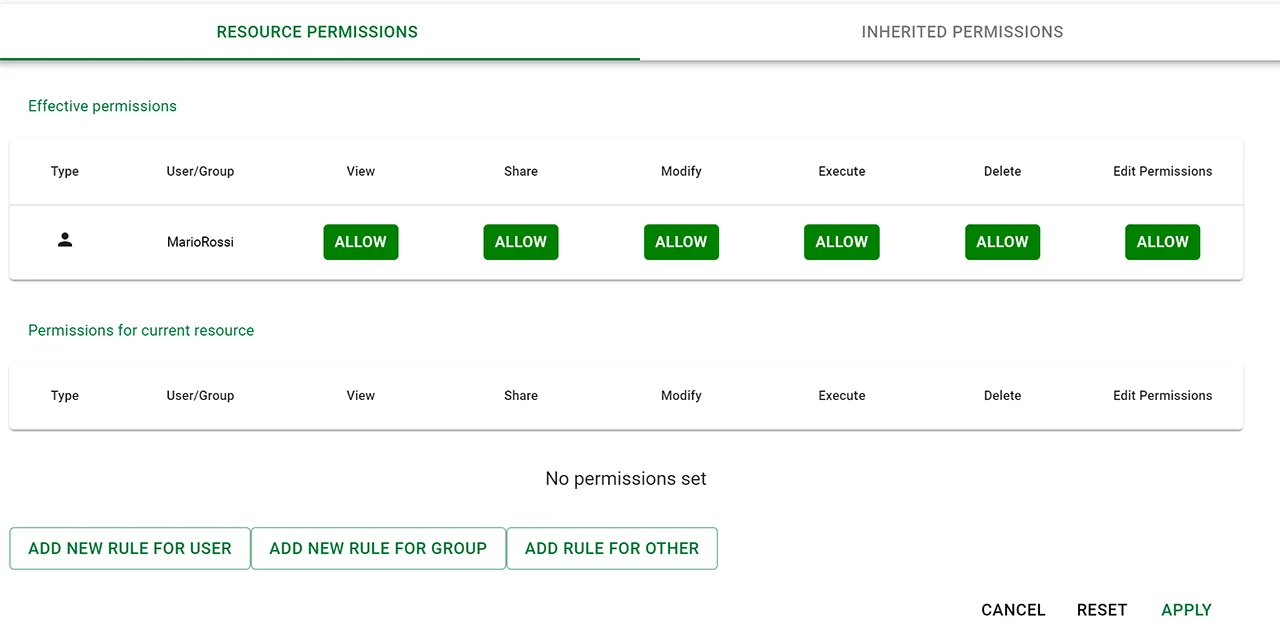
Granular role and permission management via Rulex Platform’s interface.
Rulex Platform is also ISO 27001 certified, aligning with globally recognized standards for information security management.
Build lasting customer trust
In an era where data breaches make headlines, implementing a strong data governance and security framework has become a business necessity.
Define custom roles and permissions, keeping an eye on all access and changes, and lock down your data with top-notch security and encryption. Request a 30-day Rulex Platform free trial now.
Securely manage your data down to the finest detail with Rulex Platform








